Roles
Roles and configurations are different items. A role has various performance groups of counters, services, events, alarms etc. that may be needed on a particular system. Configurations are a collection of roles. (See Creating a New Configuration). When the creation of the configuration containing roles is completed, it can then be attached to a specific child machine or group of machines using Assignments.
SysTrack role-based configurations allow you to add system security measures to one or many systems quickly and easily. A role is layered on top of an existing configuration to allow you to add flexibility. For example, a laptop and Exchange server configuration may be vastly different; both can have the same enterprise security role layered on top for identical security tracking.
-
Click the lock icon on the top right of the page to unlock Configure for editing.
-
In System Configuration, click Roles.
-
(Optional) Click Show Factory Roles to add SysTrack factory roles to the drop down list on the left. Although factory roles cannot be edited or deleted, using a duplicate can provide a good starting point when creating a new role.
- To configure a new role, click the + (plus) icon to display the Create New Role dialog. Alternately, you can click the
 (duplicate) icon and rename and amend an existing role to your specifications.
(duplicate) icon and rename and amend an existing role to your specifications. - Enter a name for the role, and click Create.
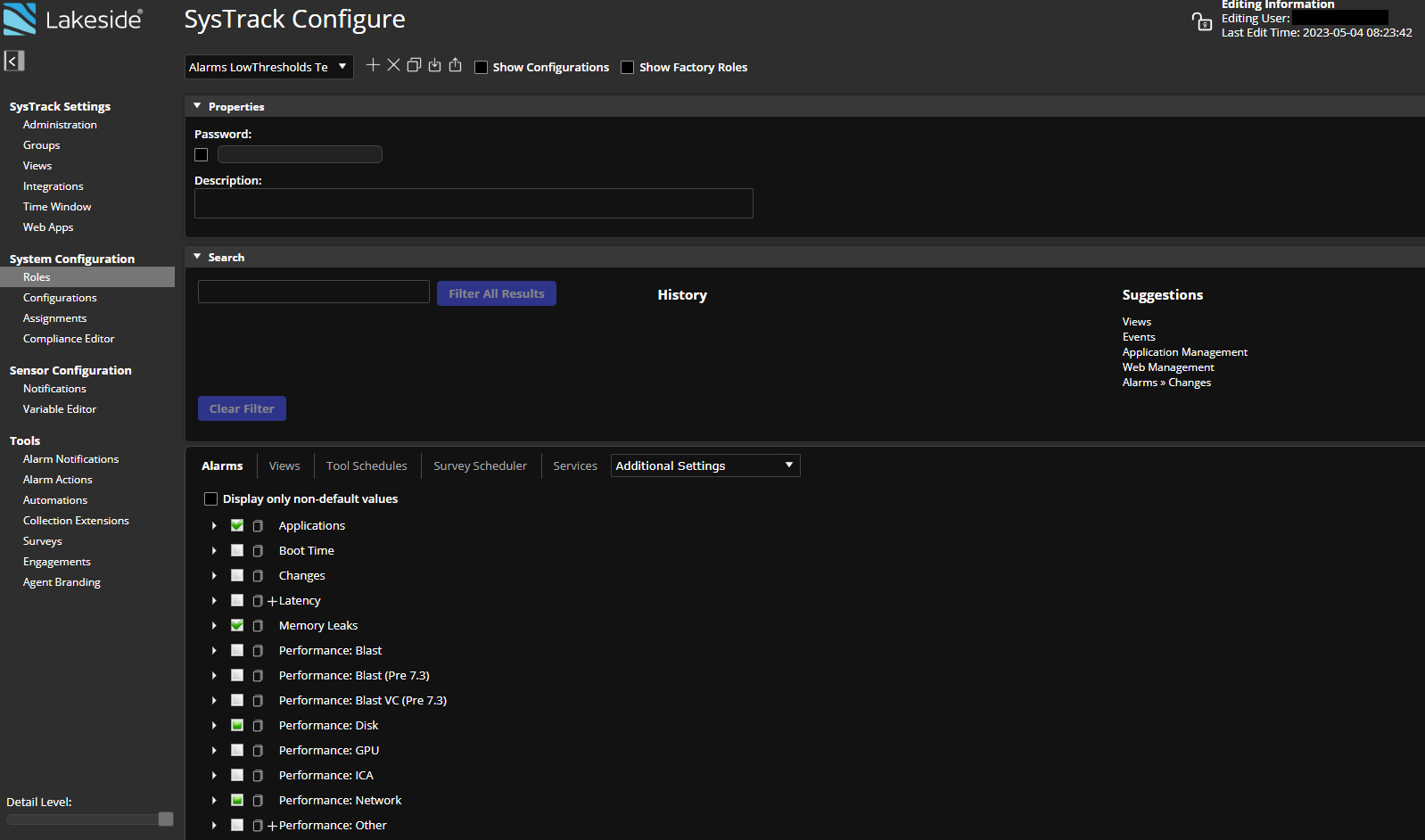
The following configuration options are available from the Roles page:
- Password protection
- Alarms
- Policies
- Events
- Inventory
- Scripting
- Power Management
- Quality of Service
- Views
- Survey Scheduler
- Tray App
- Automations
- Health
Topics in This Section
On This Page