Memory Leaks Alarms
A memory leak occurs when a program repeatedly allocates memory resources for use and fails to release the memory resource when the work it was performing is completed. If the allocation of memory is small and not a commonly called item in the program, a memory leak may go undetected for the life of a program. However, most memory leaks are persistent in that the allocation happens repeatedly. System performance will degrade as more and more memory is consumed. Other applications may fail, and seemingly without cause or reason, because of this.
Using this category on the Roles page Alarms tab, you can configure the memory leak alarms.
In the example alarm configuration called out below, if a memory leak is detected that is higher than 0.2 KB per minute (with a sensitivity level of 85%), an alarm will be triggered and a Notification will be sent.
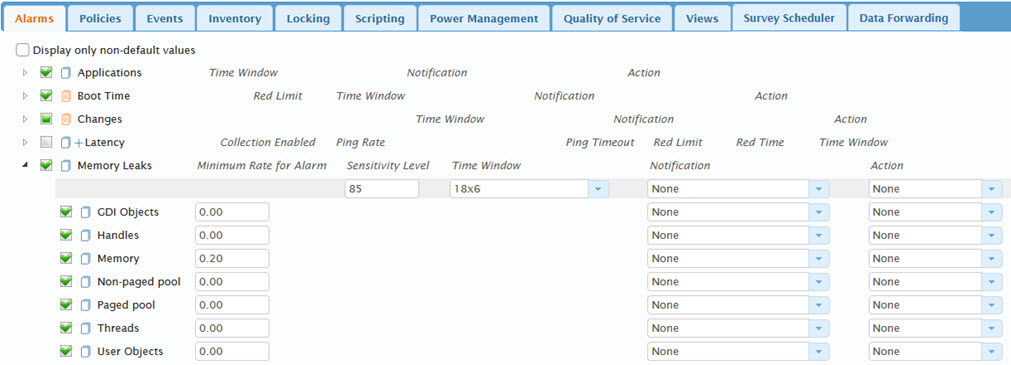
The following table defines each of the memory leak detection alarms.
| Memory Leak Alarm | Description |
|---|---|
| GDI Objects | Monitors detected GDI object leaks. A GDI Object is an object from the Graphics Device Interface (GDI) library of application programming interfaces (APIs) for graphics output devices. This is the measurement, in kilobytes per minute, of GDI object leaks on any Windows-based application. No leaks are preferred. |
| Handles | Monitors detected handle leaks. A handle leak occurs when a computer program asks for a handle to a resource but does not free the handle when it is no longer used. If this occurs frequently or repeatedly over an extended period of time a large volume of handles may be marked in-use and as a result, unavailable. This can cause performance problems or a crash. No leaks are preferred. |
| Memory | Monitors detected memory leaks. Memory leaks are failures to release unused memory by a computer program. It is just unnecessary memory consumption. A memory leak occurs when the program loses the ability to free the memory. A memory leak diminishes the performance of the computer, as it becomes unable to use all its available memory. Excessive memory leaks can lead to program failure after a sufficiently long period of time. Smaller is better. |
| Non-paged Pool | Monitors detected non-paged pool leaks. These are a measurement, in bytes per minute, of memory leaking non-paged or non-paging data on any Windows-based application. Non-Paged Pool Memory is typically a smaller pool of memory and cannot be paged out to disk. The Non-paged pool is set virtual memory pages that always remain resident in RAM. Device drivers and the OS use the non-paged pool to store data structures that must stay in physical memory and can never be paged out to disk. (For example, the TCP/IP driver must allocate some amount of non-paged memory for every TCP/IP connection that is active on the computer for data structures that are required during processing of network adapter interrupts when page faults cannot be tolerated.) A device driver with a memory leak will eventually exhaust the supply of Non-paged Pool Memory, which will cause subsequent allocations that request the non-paged pool to fail. Running out of space in the non-paged pool almost always results in a Blue Screen. No leaks are preferred. |
| Paged Pool | Monitors detected paged pool leaks. These are a measurement, in bytes per minute, of memory leaking paged data on any Windows-based application. Paged Pool Memory can be paged out to disk. Virtual memory for various system functions, including shared memory files (like DLLs), is allocated from the Paged Pool, which is an area of the system's virtual memory that is limited in size. A program with a memory leak that is allocating, but never freeing memory from the Paged Pool will eventually exhaust the Paged Pool. Subsequent allocations that request the Paged Pool will then fail, with unpredictable results causing applications to act erratically and in some cases failing. No leaks are preferred. |
| Threads | Monitors detected Java thread leaks. |
| User Objects | Monitors detected user object leaks. A User Object is an object from Windows Manager which includes windows, menus, cursors, icons, hooks, accelerators, monitors, keyboard layouts, and other internal objects. This is the measurement, in kilobytes per minute, of user object leaks on any Windows-based application. No leaks are preferred. |
Configure Memory Leak Detection Alarms
- Select the check box to the left of the Memory Leaks category to apply the same configuration to the individual alarms.
- To change a Minimum Rate For Alarm value, click the value, then enter the updated value. This is a measurement that, in kilobytes per minute, that the SysTrack Agent uses to determine if a memory leak is occurring.
- Selecting the check box to the left of an alarm will generate an alarm when the Minimum Rate For Alarm is exceeded. By default, all alarms are enabled.
- Select a Notification profile to use for the alarm notification settings that will be followed when the alarm is triggered.
- Select a Time Window for the alarm.
- Select an Action profile to use when the alarm is triggered.
- Use the Sensitivity Level to set the sensitivity degree of monitoring that the SysTrack Agent will employ. A process that is using memory repeatedly may not be suffering a memory leak. It may be part of the design and is self-terminating when a certain condition is met. The sensitivity level can help take into account conditions where memory consumption can be expected for short periods of time. The default setting is 85.
On This Page